
DFARS 7019 Compliance: What Defense Contractors Need to Know
In November 2020, the U.S. Department of Defense (DoD) announced the Defense Federal Acquisition Regulation Supplement (DFARS) Interim Rule. The DFARS Interim Rule establishes the Cybersecurity Maturity Model Certification (CMMC) as the cybersecurity framework for contractors and suppliers in the Defense Industrial Base (DIB). The Interim Rule requires defense contractors handling controlled unclassified information (CUI) to implement the cybersecurity controls described in the National Institute of Standards and Technology Special Publication 800-171 (NIST SP 800-171). The Interim Rule strengthens the self-assessment requirements of NIST SP 800-171 as contractors transition to CMMC 2.0 certification.
The DFARS Interim Rule contains three clauses: 252.204-7019, 7020, and 7021. In this blog post, we will take a deeper look into clause 7019, which basically requires defense contractors to:
- Conduct a self-assessment of NIST SP 800-171 compliance in accordance with the DoD Assessment Methodology
- Report the scores from this assessment to the DoD through the Supplier Performance Risk System (SPRS)
What Is DFARS 7019?
As part of the DFARS Interim Rule, DFARS clause 7019 requires all DoD contractors to comply with the cybersecurity standards outlined in NIST SP 800-171. This clause is part of the DoD’s efforts to enhance the protection of CUI and other sensitive government information from cyber threats and attacks.
Clause 7019 was added to DFARS to address the security of CUI in non-federal systems and organizations. This clause requires contractors and subcontractors to implement specified security controls to safeguard CUI, and to report any security incidents that may compromise the confidentiality, integrity, or availability of CUI. Unlike clause 7020, which focuses on safeguarding classified information, and clause 7021, which applies to the protection of unclassified controlled technical information (UCTI), clause 7019 specifically targets the protection of CUI. Additionally, clause 7012 pertains to the protection of Controlled Defense Information (CDI) and requires contractors and subcontractors to implement certain security controls as well as report any incidents that may affect the confidentiality, integrity, or availability of CDI. While both clauses 7019 and 7021 address information security, they are distinct in their focus on protecting different types of sensitive information.
How Do DFARS 7019 and CMMC Overlap?
DFARS 7019 and CMMC overlap in the sense that both are related to cybersecurity requirements for DoD contractors. DFARS 7019 is a clause that requires contractors to have a cybersecurity plan in place, while CMMC is a framework that assesses a contractor’s cybersecurity practices and assigns a certification level based on their maturity and compliance with cybersecurity requirements. CMMC 2.0 has three levels of compliance that include CMMC 2.0 Level 1 (Foundational), CMMC 2.0 Level 2 (Advanced), and CMMC 2.0 Level 3 (Expert).
In other words, DFARS 7019 is a requirement for contractors to have a cybersecurity plan, and CMMC is a certification process that assesses and validates the effectiveness of that plan. CMMC builds on the DFARS 7019 requirement and adds additional security controls and practices to ensure contractors meet a higher level of cybersecurity maturity.
Why Is DFARS 7019 Compliance Important?
DFARS clause 7019 is a crucial requirement for defense contractors who work on DoD-sponsored projects. Compliance with this clause is mandatory, and it is vital for several reasons.
One of the critical reasons that DFARS 7019 compliance is essential is cybersecurity. Defense contractors who wish to comply with this clause must have adequate cybersecurity measures in place to protect sensitive information related to national security. With the increase in cyberattacks and data breaches, it is crucial to have effective cybersecurity measures in place to prevent unauthorized access to sensitive information.
Compliance with DFARS 7019 helps to build trust and credibility with the DoD and other contractors in the industry. It shows that defense contractors take their responsibilities seriously and are committed to protecting sensitive information related to national security. Compliance with DFARS 7019 also boosts a contractor’s reputation in their own industry and may provide a competitive advantage when competing for non-DoD jobs.
DFARS 7019 Requirements
DFARS 7019 sets forth some essential requirements for defense contractors. First and foremost, contractors must implement the security controls specified in NIST SP 800-171, which consists of 110 security requirements spread across 14 different families. These families include access control, identification and authentication, risk assessment, and security assessment, among others. While some of the requirements may be relatively straightforward to implement, others may prove to be more challenging, depending on the size and complexity of the contractor’s organization and information systems.
DFARS 7019 also requires defense contractors to undergo assessment based on the NIST SP 800-171 methodology. This assessment will result in a score ranging from -203 to 110, with a higher score indicating better compliance with NIST SP 800-171 requirements. Defense contractors must then submit their score along with a System Security Plan (SSP) and Plan of Action and Milestones (POA&M) to the Supplier Performance Risk System (SPRS). The DoD will use these scores to evaluate the risk associated with awarding contracts to different defense contractors.
What Is the Role of the DCMA in DFARS 7019 Compliance?
The Defense Contract Management Agency (DCMA) is responsible for ensuring that contractors comply with the requirements of DFARS 7019. To achieve this, the DCMA conducts audits and assessments of contractors to ensure they are implementing appropriate controls and processes to protect unclassified controlled technical information (UCTI).
The DCMA also provides guidance and training to contractors on how to comply with DFARS 7019 and assists in the development and implementation of UCTI protection plans. Additionally, the DCMA may provide support and assistance to contractors in the event of a cybersecurity incident or breach.
DCMA Audit Process for DFARS 7019 Compliance
The DCMA conducts audits to ensure defense contractors’ compliance with DFARS 7019. These audits evaluate contractors’ cybersecurity measures and assess their compliance with the NIST SP 800-171 guidelines. The DCMA may also conduct audits to verify contractors’ self-assessment of their compliance with DFARS 7019.
During an audit, the DCMA will review documentation related to the contractor’s cybersecurity measures, including policies, procedures, and system security plans. The auditor may also conduct interviews with employees to verify the effectiveness of the contractor’s cybersecurity measures.
If the DCMA identifies noncompliance during an audit, it will issue a Corrective Action Request (CAR). The contractor must respond to the CAR and take corrective measures to address the noncompliance. Failure to comply with a CAR may result in penalties or termination of the contract.
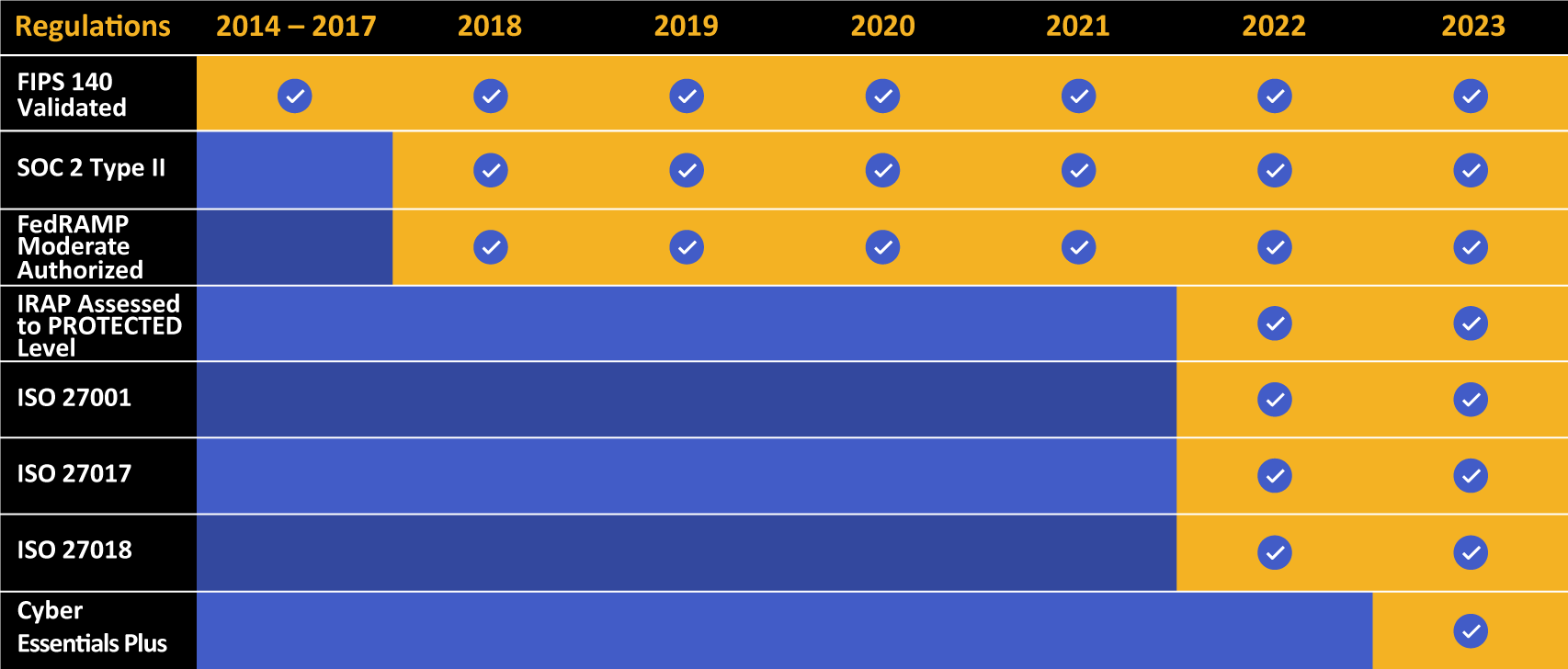
Kiteworks touts a long list of compliance and certification achievements.
What Are Some of the Challenges in Complying With DFARS 7019?
Defense contractors may face several challenges in complying with DFARS 7019, such as limited resources, lack of expertise, and resistance to change. Smaller contractors, in particular, may struggle to allocate the necessary resources and personnel to address the numerous security requirements outlined in NIST SP 800-171. Furthermore, interpreting and implementing these requirements can be a daunting task for organizations that do not have in-house cybersecurity expertise.
Another potential challenge is resistance to change within the organization. Implementing the required security controls may necessitate significant adjustments to existing workflows, processes, and even company culture. Defense contractors must be prepared to effectively manage this resistance and foster a culture of cybersecurity awareness and compliance across all levels of the organization. Ultimately, failure to comply with DFARS 7019 can lead to severe consequences, including the loss of valuable contracts with the DoD, financial penalties, and damage to the organization’s reputation and standing in the defense industry.
Best Practices for Achieving Compliance With DFARS 7019
There are several steps defense contractors can take to facilitate a smooth DFARS 7019 compliance process. Consider the following recommendations as best practices for DFARS 7019 compliance:
| Understand the Requirements | Familiarize yourself with the DFARS 7019 requirements and what they mean for your organization. Ensure that all relevant stakeholders in your organization are aware of these requirements. |
| Conduct a Thorough NIST SP 800-171 Gap Analysis | To identify where their information systems may be lacking in terms of security controls. This assessment should involve both technical and non-technical stakeholders to ensure a comprehensive understanding of the organization’s cybersecurity posture. |
| Develop a Plan | Create a roadmap to achieve compliance, including timelines, tasks, and responsibilities. Develop a plan for ongoing monitoring and maintenance of compliance. |
| Train Employees | Educate your employees on the DFARS 7019 requirements and how they can contribute to compliance efforts. Ensure that all employees are aware of their roles and responsibilities in achieving compliance. |
| Implement Security Controls | Put in place appropriate security controls to protect sensitive information and comply with the DFARS 7019 requirements. This may include implementing access controls, encryption, and other measures. |
| Conduct Regular Audits | Regularly conduct audits to ensure that your organization remains compliant with DFARS 7019. This will help you identify areas where you may need to make improvements. |
| Report Incidents | In case of any incident, ensure that it is reported to the relevant authorities in a timely manner. This will help you avoid penalties and maintain compliance with DFARS 7019. |
| Engage With Suppliers | Ensure that your suppliers are also compliant with DFARS 7019. Engage with them and work together to ensure that all requirements are met. |
| Stay Updated | Stay updated on any changes to DFARS 7019 or other regulations that affect your organization. This will help you stay ahead of any compliance issues. |
Your DFARS 252.204-7019 Compliance Journey Begins With Kiteworks
Defense contractors looking to comply with DFARS 7019 should consider the Kiteworks Private Content Network (PCN). Because Kiteworks is FedRAMP Authorized to Moderate Level Impact, it meets all the security requirements listed in NIST SP 800-171. This not only allows defense contractors to share and transfer CUI with government agencies, but does it with the highest levels of security and compliance. Kiteworks also supports nearly 90% of CMMC 2.0 Level 2 requirements out of the box, the highest level for sensitive content communications platforms in the industry.
The Kiteworks PCN is a unified, secure, and easy-to-use communications platform that provides end-to-end encryption, secure access controls, encryption key ownership, and visibility into all file activity. Kiteworks consolidates all third-party communication channels, including secure email, file sharing, managed file transfer (MFT), secure file transfer protocol (SFTP), web forms, and more so that every sensitive file sent, received, or shared is centrally controlled, protected, monitored, and tracked.
With Kiteworks’ PCN, every file upload, download, and share is logged for eDiscovery and regulatory compliance. Kiteworks also supports a range of other regulations and standards, including International Traffic in Arms Regulations (ITAR), the General Data Protection Regulation (GDPR), SOC 2, the Federal Information Security Management Act (FISMA), FIPS 140-2, and Export Administration Regulations (EAR).
For more information on the Kiteworks platform, schedule a custom demo today.
Additional Resources
- Article Protecting CUI With NIST SP 800-171: How to Stay Compliant
- Blog Post What Are Data Compliance Standards?
- Blog Post Secure File Transfer for Defense Contractors: Ensuring Confidentiality and Integrity
- Blog Post NIST 800-171 Compliant File Sharing—What You Need to Know and How Kiteworks Can Help
- Blog Post A Roadmap for CMMC 2.0 Compliance for DoD Contractors